Lecture
Contributors: Alicia Wang, Conner Swenberg
Lecture Slides
Integrating a Database
Readability
SELECT Country.name, T.language
FROM country Country, countrylanguage CL2,
(SELECT tmp.language, code FROM country,
(SELECT CL.language, MAX(C.surfacearea)
FROM country C, countrylanguage CL
WHERE C.code=CL.countrycode
GROUP BY CL.language) as tmp
WHERE (surfacearea = tmp.max)) T
WHERE T.code = Country.code
AND T.language = CL2.language
AND Country.code = CL2.countrycode;Runtime Errors
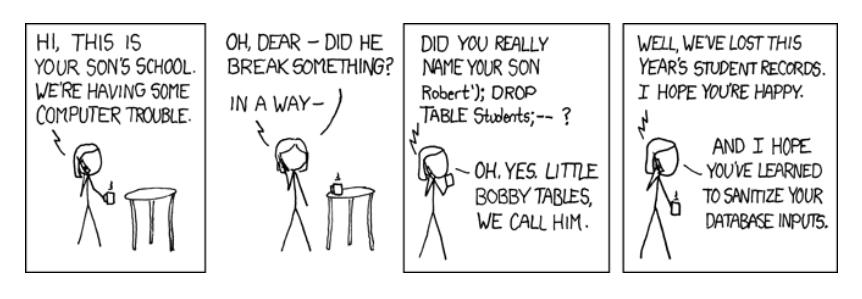
Vulnerabilities
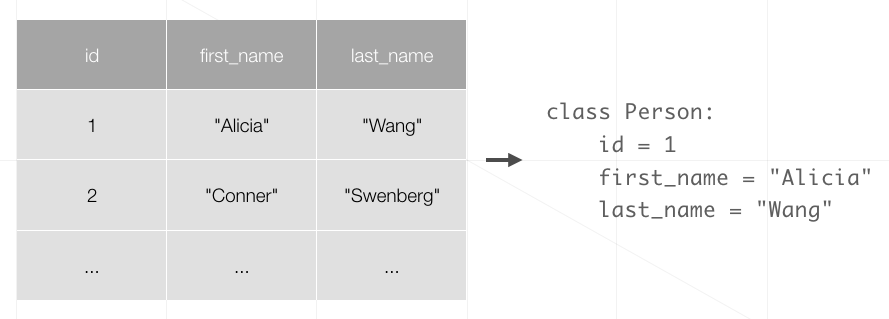
Object Relational Mapping
Last updated
Was this helpful?